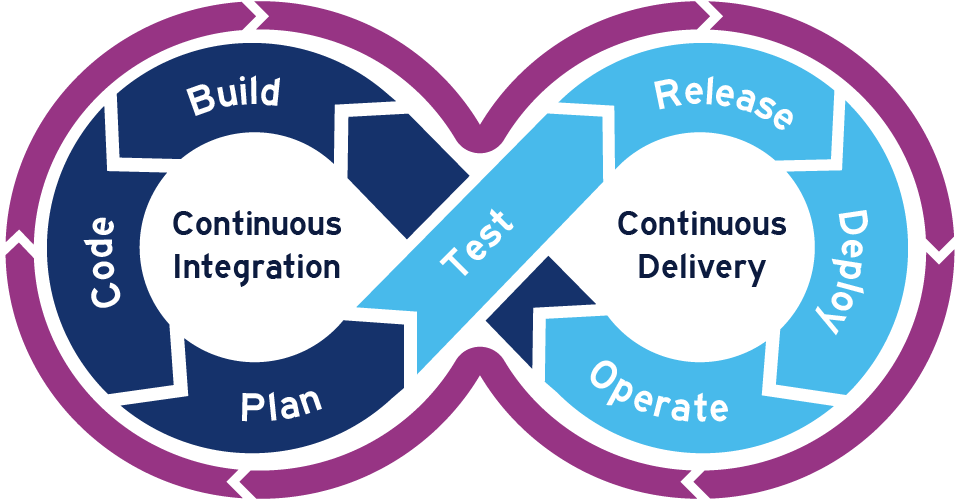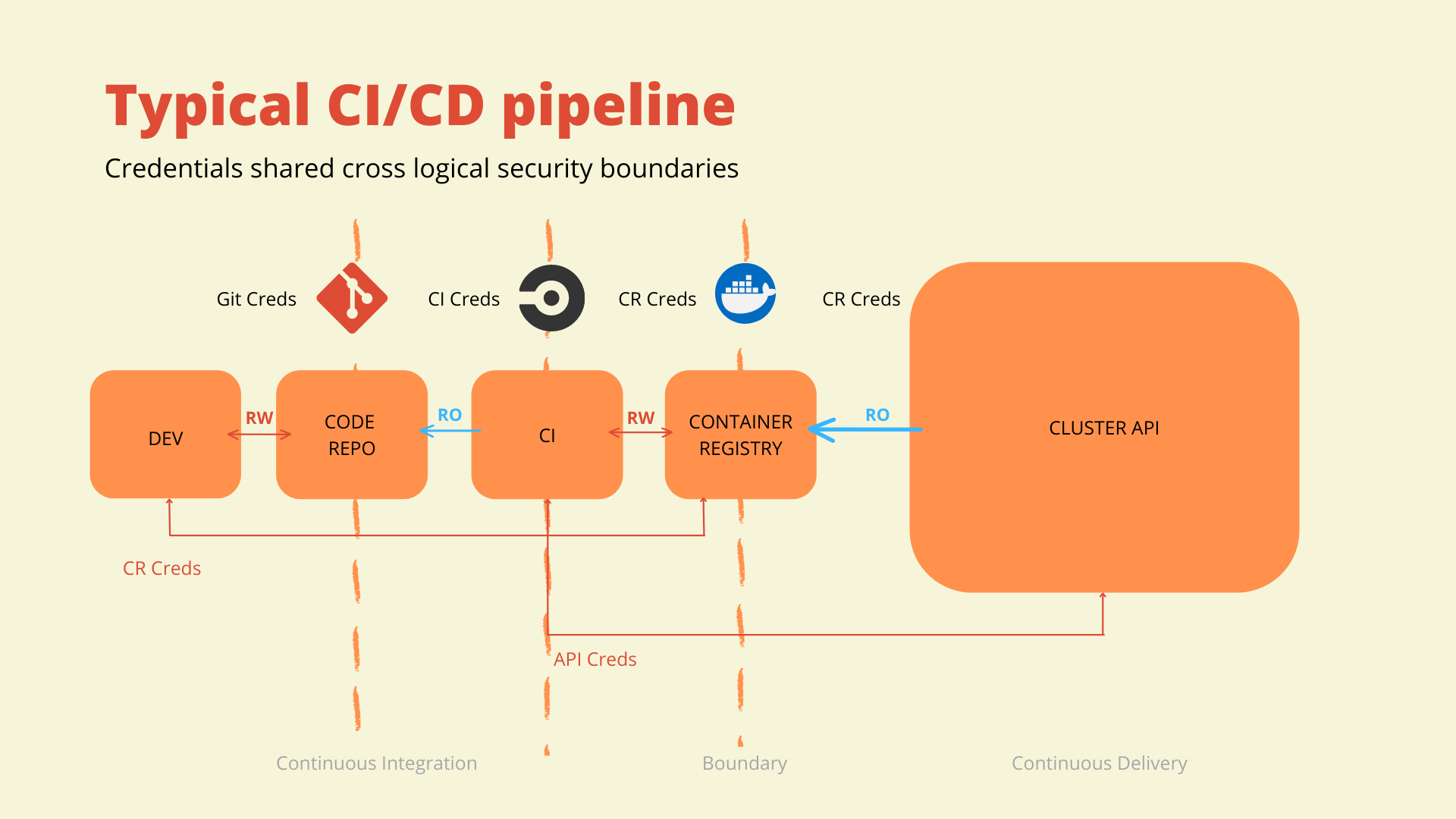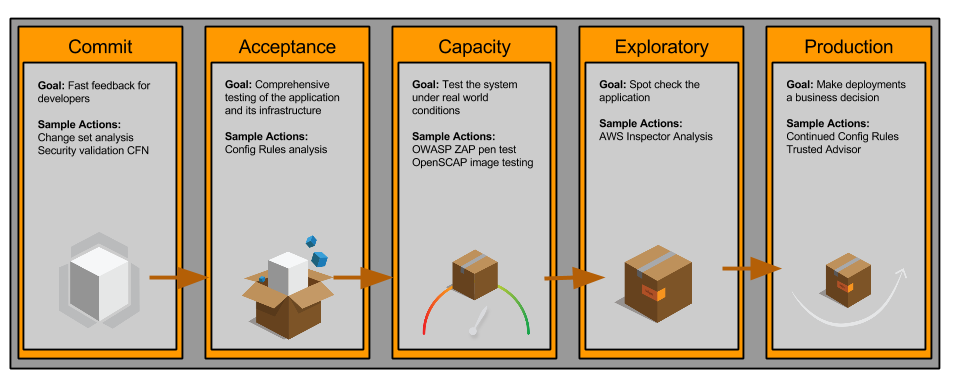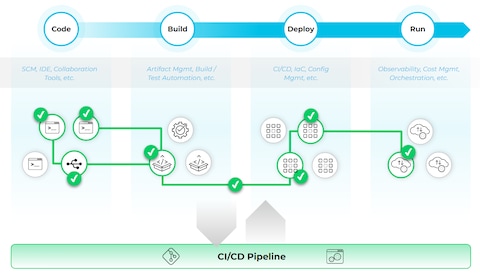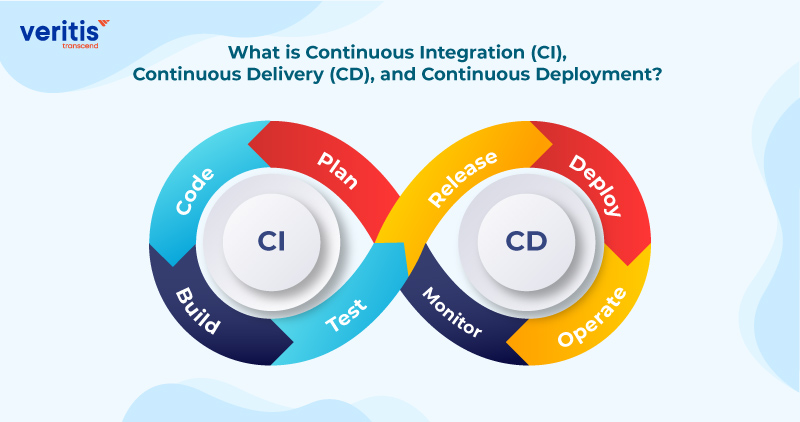
Azure Security Best Practices for DevOps and Continuous Integration/Continuous Deployment (CI/CD) - HailBytes

Cybersecurity and Infrastructure Security Agency on X: "Our new guidance with @NSACyber can help organizations secure their continuous integration/ continuous delivery (CI/CD) environments. Learn about this threat and take our recommended mitigations steps: