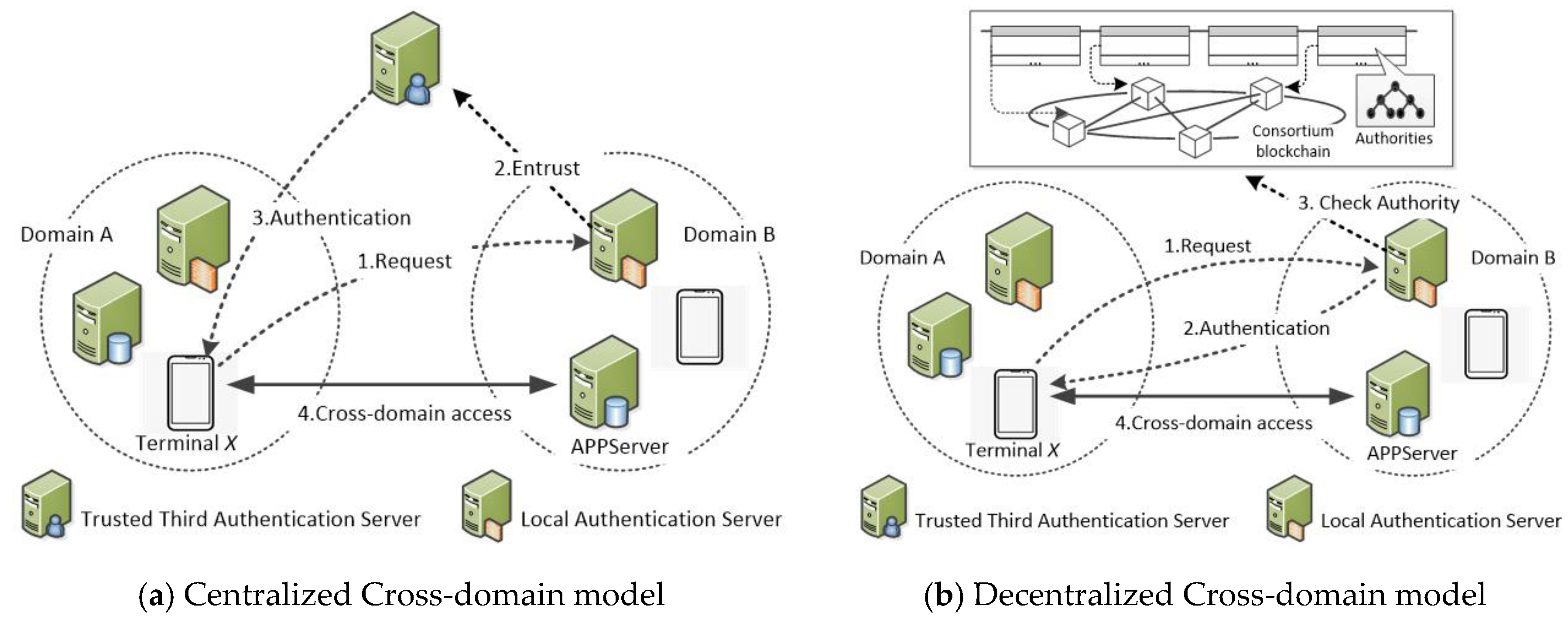
Electronics | Free Full-Text | IRBA: An Identity-Based Cross-Domain Authentication Scheme for the Internet of Things

security - The best approach to manage centralized authentication/authorization to in-house mutiple API? - Stack Overflow

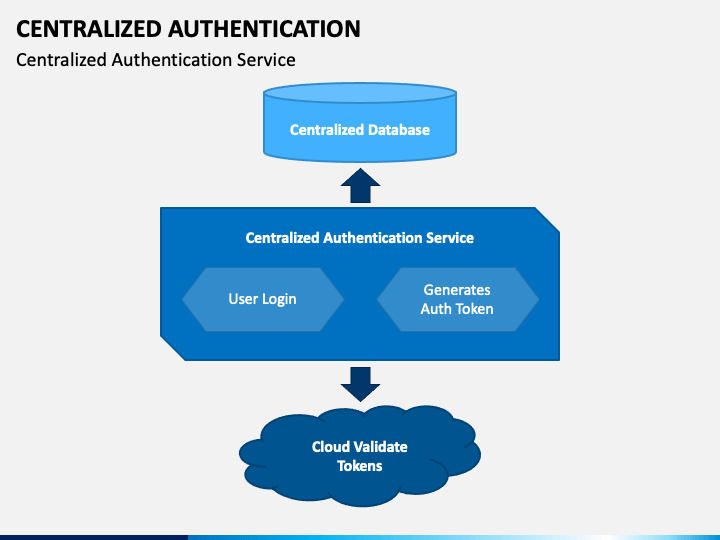
Centralized authentication - Web Site Srl | the software house that can help you to build, on advanced technological platforms, enterprise-level systems
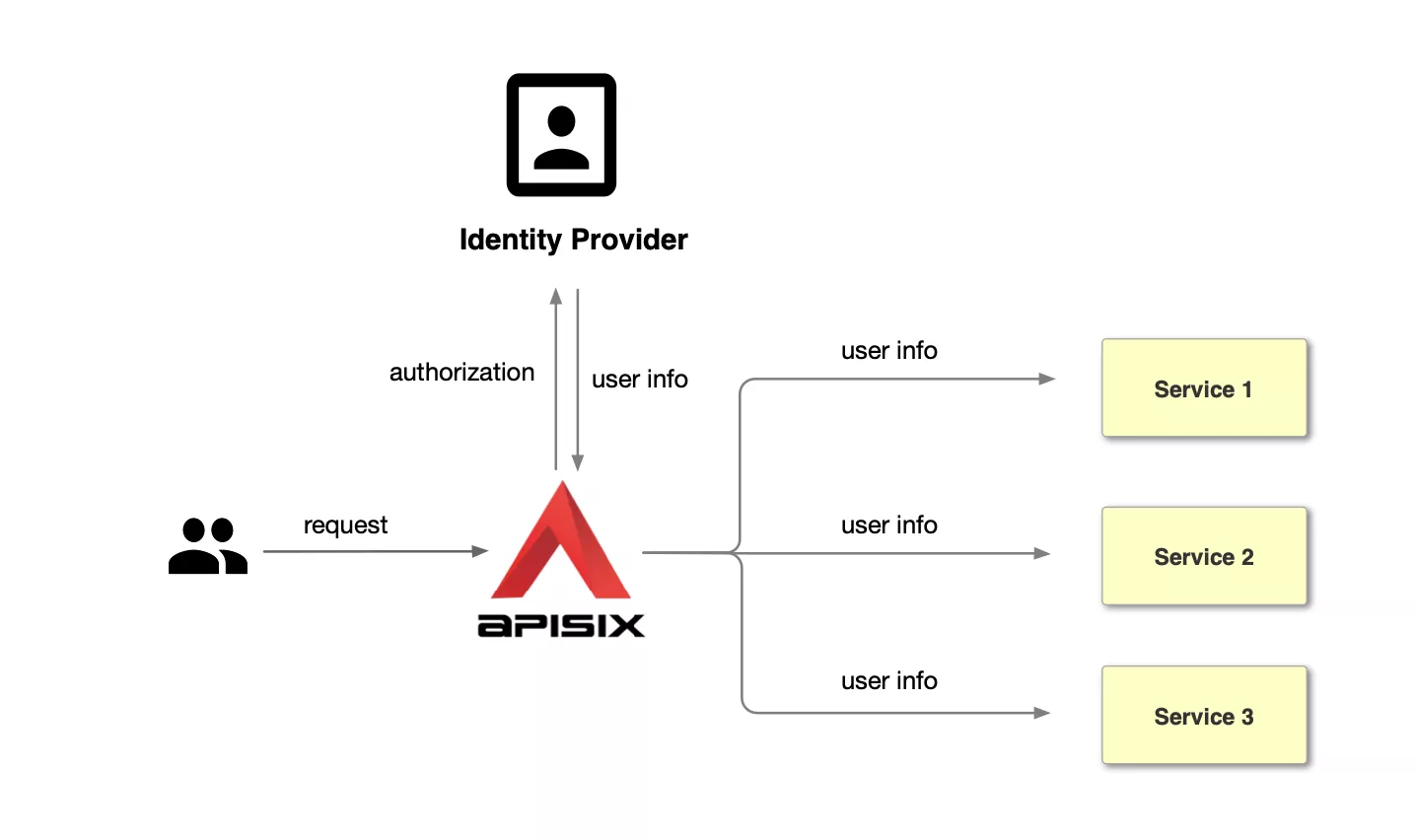
Centralized authentication using the OpenID Connect plugin for Apache APISIX | Apache APISIX® -- Cloud-Native API Gateway
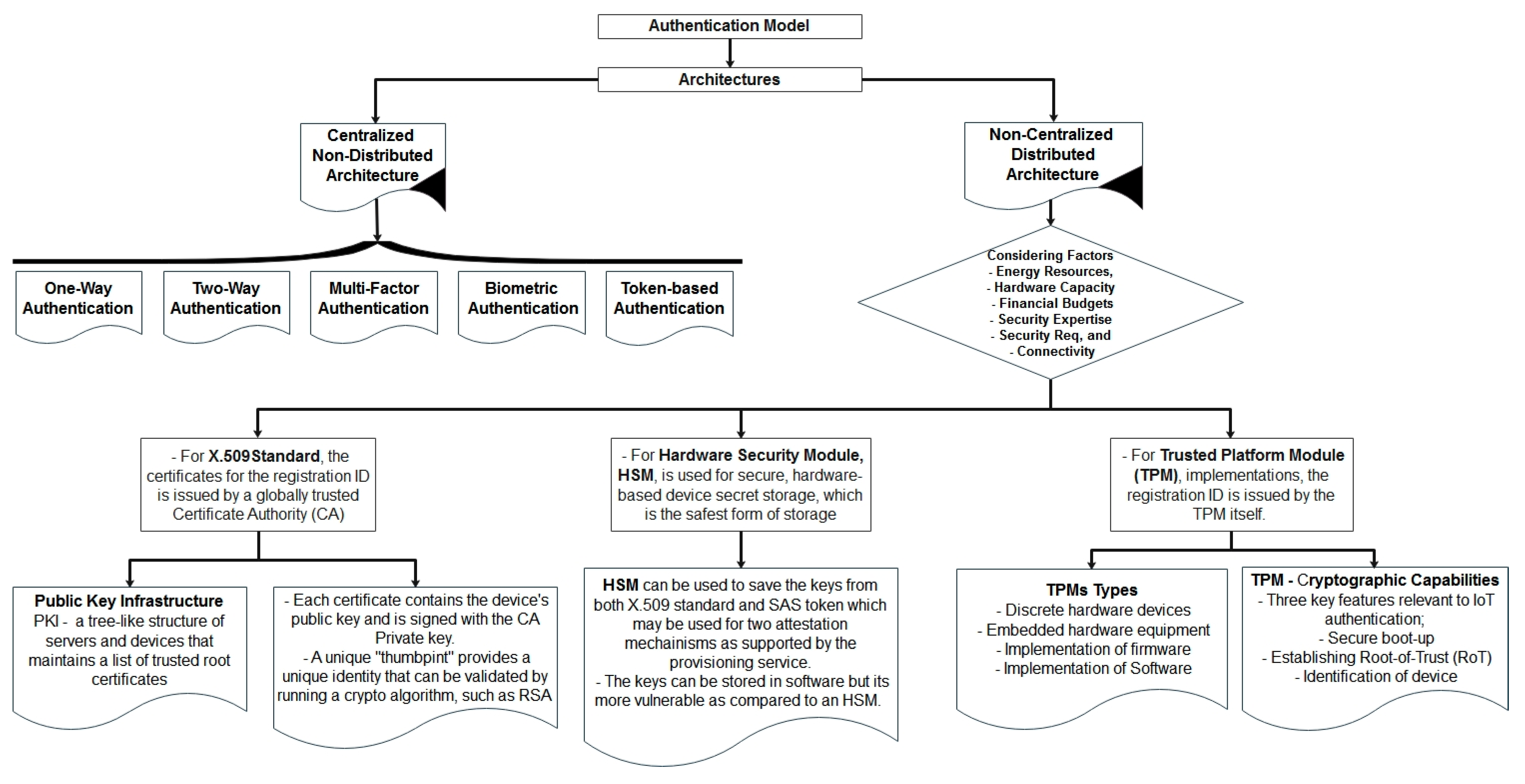
Sensors | Free Full-Text | A Comparative Analysis on Blockchain versus Centralized Authentication Architectures for IoT-Enabled Smart Devices in Smart Cities: A Comprehensive Review, Recent Advances, and Future Research Directions

Figure 1.4 from User Identification and Authentication Concepts 1.1 Security Landscape | Semantic Scholar